An Air Force officer’s computer was purportedly hacked, compromising a cache of sensitive documents relating to the MQ-9 Reaper, which were then put up for sale on the dark web in June.
Also for sale: an Army M1 Abrams tank operation manual.
The Air Force compromise was easily preventable, according to a report by Recorded Future, the private threat intelligence firm that intercepted the hacked documents and alerted authorities.
“The captain whose computer was compromised recently completed the Cyber Awareness Challenge and should have been aware of the required actions to prevent unauthorized access,” the report reads. “In this case, setting the FTP password.”
The hacker used a well-known tactic of gaining access to vulnerable Netgear routers with improperly setup login credentials.
With the help of a popular search engine that lets users find specific types of webcams, routers and servers, known as Shodan, the hacker was able to scan large segments of the Internet for high-profile, improperly configured routers to hijack valuable documents.
RELATED

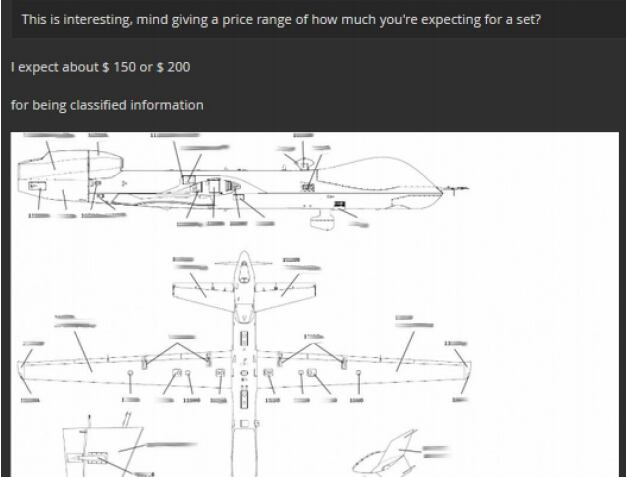
Utilizing that method, the hacker gained access to a computer belonging to a captain at the 432nd Aircraft Maintenance Squadron at Creech Air Force Base, Nevada. They then stole a cache of sensitive documents, including Reaper maintenance course books and a list of airmen assigned to the Reaper aircraft maintenance unit at Creech.
“While such course books are not classified materials on their own, in unfriendly hands, they could provide an adversary the ability to assess technical capabilities and weaknesses in one of the most technologically advanced aircraft,” Recorded Future said in its report.
Netgear reported the vulnerability in its routers in 2016, and outlined a series of steps to address the issue:
- Launch an Internet browser from a computer or wireless device that is connected to the network.
- Type in http://www.routerlogin.net or http://www.routerlogin.com. A login screen will display.
- Enter the router username and password. The username is admin. The default password is password. The username and password are case sensitive. The BASIC home screen will display.
- Select ADVANCED > USB Functions > ReadySHARE Storage.
- Select FTP.
- Click Apply.
Recorded Future noticed the drone documents advertised on the dark web, and made contact with the seller, who was seeking about $150 to $200 for the information.
The seller also advertised the sale of training manuals describing tactics to defeat improvised explosive devices, an M1 Abrams tank operation manual, a crewman training and survival manual, and tank platoon tactics documents.
“As with the previous documents, none represent classified materials, although most can be distributed to U.S. government agencies and their contractors only,” Recorded Future said.
Although the seller didn’t disclose how he acquired these manuals — as he had with the drone documents — Recorded Future assessed that they appeared to be stolen from a Pentagon or U.S. Army official.
The firm reported the attempted sale to the Defense Security Service, a federal security agency within the Department of Defense. However, Recorded Future couldn’t put Miltiary Times in touch with the officials who were responding to the incident.
“We cannot provide specific details, but we directly contacted [Defense Security Service], which, to the best of our knowledge, handles this type of information for DoD,” the company said in an emailed statement. “We also contacted several other government customers, but cannot go into the details of who that may be.”
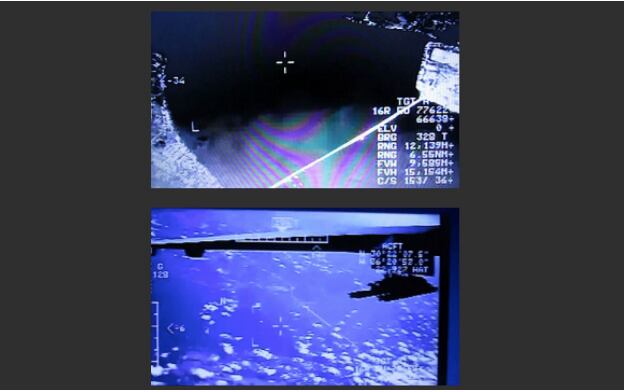
During the firm’s talks with the hacker, he said that on days he was not hunting for his next victim, he entertained himself by watching live footage from border surveillance cameras and airplanes. He went as far as bragging about accessing footage from a MQ-1 Predator flying over Choctawhatchee Bay along Florida’s panhandle.
These allegations have not been confirmed, but Recorded Future did provide screenshots of their conversation and some of the hacked feeds.
Kyle Rempfer was an editor and reporter who has covered combat operations, criminal cases, foreign military assistance and training accidents. Before entering journalism, Kyle served in U.S. Air Force Special Tactics and deployed in 2014 to Paktika Province, Afghanistan, and Baghdad, Iraq.





